JWT Essentials: A Beginner’s Guide for Developers & QAs
- 05 Sep, 2025
JWT authentication and session authentication are two common methods to authenticate users in your web application and have become a key part of secure and efficient token-based authentication. JWTs provide a compact, self-contained way to transmit information securely between two parties, ensuring data integrity and authenticity without the complexity of managing server-side session states.
This post will walk you through the fundamentals of JWT authentication: key concepts, structure, use cases, and practical workflows. Let’s start!
What is JWT?
JWT stands for JSON Web Token. It is a widely used, stateless authentication standard that securely transmits information between client and server in JSON format.
JSON Web Tokens are used to share information between two entities, usually a client (such as your app’s frontend) and a server (your app’s backend).
What is a token and why is it needed?
A token is a string that securely carries information between parties. It could be a random set of alphanumeric characters that point to an ID in your database, or it could be an encoded JSON object that can be self-verified by the client (known as JWTs).
By encapsulating user information, such as an email address or username within the token, the need for repeated database queries is eliminated. This reduces server load and improves response times. Due to their small size, tokens can be easily transmitted through URLs, POST parameters, or HTTP headers, making them ideal for securing API calls.
JWTs are especially useful because they contain all the necessary user info within a compact token sent with each request. This approach eliminates the need for server-side session storage, allowing each request to be independently verified.
What are JSON Web Tokens used for?
You might wonder why the authentication server can’t just send user information as plain JSON instead of a token. The reason is security: if the client receives plain JSON, there is no way to verify that the content received is authentic. For example, an attacker could change the user ID, and the application wouldn’t detect it.
JWTs solve this by digitally signing the data, allowing the client and server to verify its authenticity and integrity. This ensures that the information inside the token is trustworthy and hasn’t been altered.
Common Use Cases for JWTs
-
In distributed systems and microservices architecture: JWTs enable secure, stateless authentication across multiple services, often using private-public key signing methods. This reduces the need for repeated authentication requests and improves scalability.
-
For typical front-end to back-end communication: A JWT is used to authorize users via HTTP requests. Beyond basic authentication, JWTs can also carry user roles and permissions, enabling role-based access control in your APIs.
Structure of a JWT
Imagine a JWT as a box containing three components: Header, Payload, and Signature. These parts are Base64Url encoded and combined to form the final token.
-
Header: consists of two parts—the token type (JWT) and the signing algorithm (e.g., HMAC SHA256 or RSA). It sets the foundation for how the token will be verified.
-
Payload: contains the claims about the user or additional data. These claims can be registered, public, or private. It’s crucial to choose the correct claims and manage sensitive data carefully.
-
Signature: ensures the token’s integrity and security. The signature is generated by combining the encoded header, payload, a secret key, and the specified algorithm. This prevents tampering and verifies the token’s authenticity. Think of the signature as a special seal that only the sender knows how to create, ensuring that nobody can alter the contents of the JWT without detection.
When sending the JWT to a server, the header, payload, and signature are combined into the token. The server can then easily read the header and payload to understand who the user is and what the user wants to do.
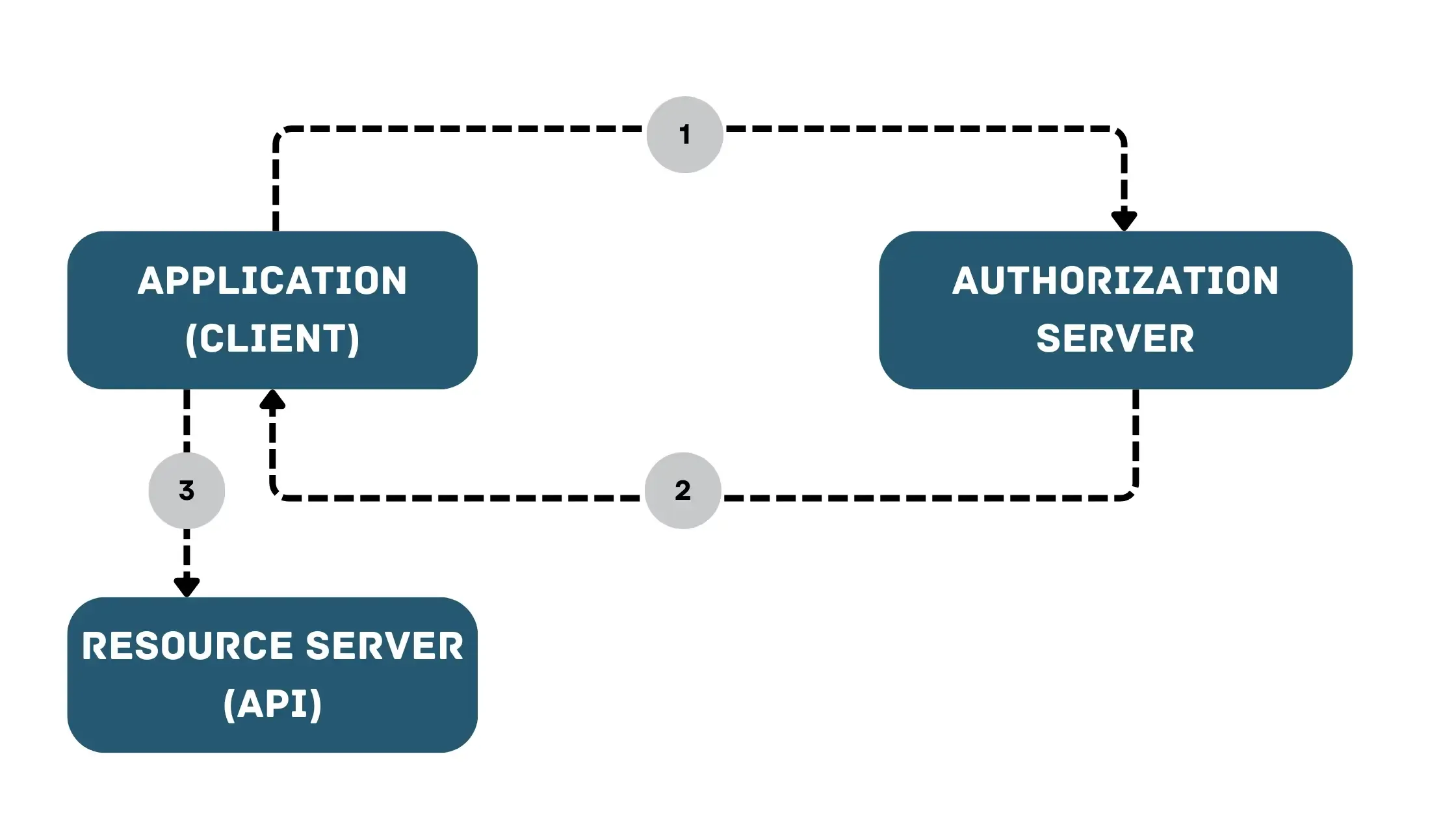
How do JWTs Work?
When a user logs into your application, the server creates a JWT and sends it to the client, which stores it (usually in local storage or a cookie). Then, for subsequent requests, the client includes this token in the Authorization header.
The server then verifies the token’s signature to confirm it’s valid and untampered, allowing it to process the request without maintaining session state. This makes authentication simpler and more scalable, especially in distributed systems.
Why Are JWTs Important for Authentication and Security?
JWTs provide numerous benefits in authentication systems:
- Stateless Authentication: No need to maintain session state on the server.
- Scalability: Suitable for microservices and distributed systems.
- Tamper Resistance and Enhanced Security: Digitally signed tokens ensure data integrity and authenticity, making them tamper-proof.
- Performance: Reduces server load and database dependencies.
- Cross-Platform Support: Easily used across web, mobile, and API ecosystems.
- Developer Convenience: Simplifies session management.
Example of a JWT
Here is a simplified example of a decoded JWT payload:
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022,
"exp": 1516242622,
"role": "admin"
}The actual JWT token is a long string like this (Base64Url encoded header.payload.signature):
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyLCJleHAiOjE1MTYyNDI2MjIsInJvbGUiOiJhZG1pbiJ9.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5cSteps in a Typical JWT Authorization Flow
Below is a simplified flow to help you understand how JWT authorization generally works:
-
Authentication: the user signs in using a username and password or via third-party providers like Google or Facebook. The server verifies the provided credentials.
-
Token Generation & Sending: upon successful authentication, the server generates a JWT and sends it to the client, which stores it securely (e.g., in an HTTP-only cookie or secure storage).
-
Sending the Token: when the client wants to access a protected resource, it includes the JWT in the Authorization header of the HTTP request:
Authorization: Bearer <token> -
Verifying the Token: the server verifies the JWT by checking its signature using the secret key or public key (depending on the algorithm). If valid, the server extracts the information contained in the token to determine the user’s permissions and grants access accordingly.
Security Tip: Avoid storing JWTs in localStorage if possible, as it is vulnerable to XSS attacks. Prefer HTTP-only, secure cookies for better protection.
Common Issues During Development
Here are some frequent JWT-related problems you might encounter:
-
JWT Rejected This error means JWT verification failed. Possible reasons include:
- The JWT has expired.
- The signature doesn’t match, indicating that signing keys have changed or the payload was tampered with.
- Claims do not match; for example, if the JWT was generated for one app (
audclaim) but is sent to another, it will be rejected.
-
JWT Token Doesn’t Support the Required Scope The token lacks the necessary permissions (scopes) for the requested operation.
-
JWT Decode Failed This error indicates the JWT is malformed and cannot be decoded properly.
-
Incorrect Key or Algorithm Using the wrong secret key or algorithm during verification will cause token rejection.
How to Validate JWTs
To ensure your JWTs are working as expected, you can use tools like JWT.io. Simply paste your JWT into the debugger to decode the payload and verify the signature.
When validating tokens, pay attention to:
- Token expiration (
expclaim) - Issuer (
iss) and audience (aud) claims - Signature validity
Final Thoughts
JSON Web Token (JWT) provides a powerful, secure, and stateless authentication method for modern web applications. It is a robust, efficient, and secure method for protecting web and mobile applications. By understanding its structure, use cases, and best practices, you can confidently implement JWTs in modern authentication systems.
Happy learning and thank you for reading!